Security Operation Centre
Functional Model (SFM)
SOC Functional Model (SFM) helps organizations to plan & prepare to set up a new SOC or to assess their existing SOC capabilities and identify the areas to focus.
Requesting the audience to understand the below topics before jumping into the described process for better understanding.
| DeTT&CT Framework | MITRE CJA | Risk Remediation Analysis |
| MITRE ATT&CK | SOC Assessment | MITRE Navigator | Threat Modeling |
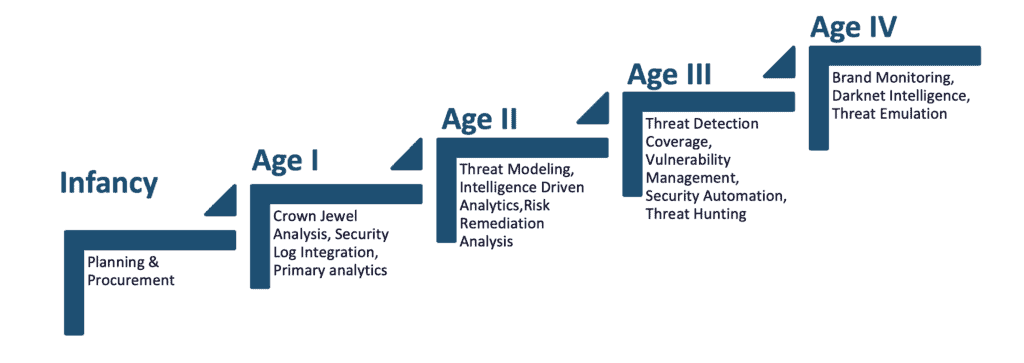
The SFM Model
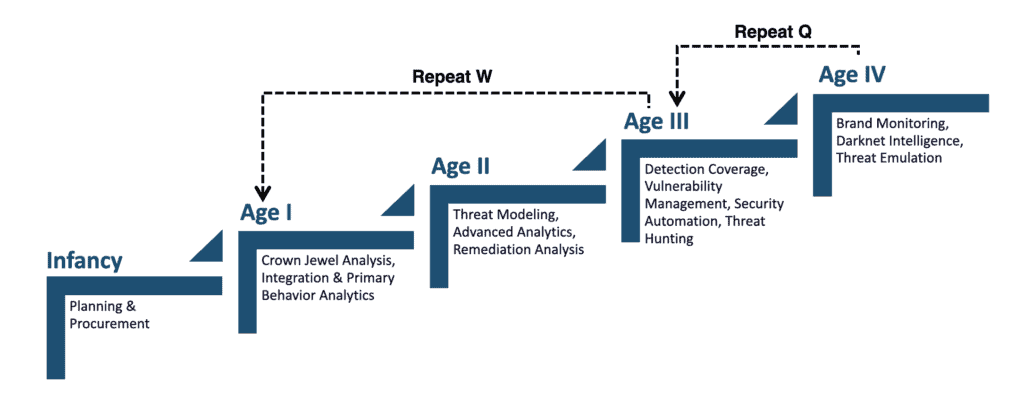
SFM consists of 5 stages to build a new SOC and 4 stages to assess your existing SOC.
Infancy
This stage applies only to organizations that are planning to set up Security Operation Centre (SOC) for the first time. The below aspects can be decided during the process of planning.
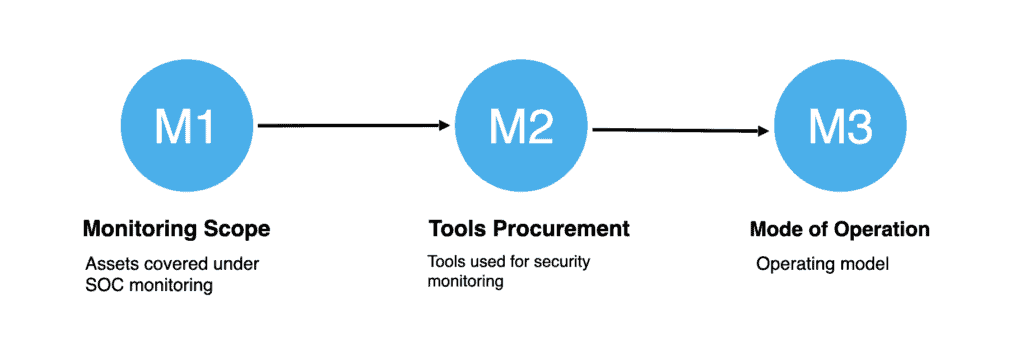
Infancy.M1 – Monitoring Scope
- SOC monitoring scope (such as only production, production + development, production + development + disaster recovery) based on business requirements.
Infancy.M2 – Tools Procurement
- Procurement of SOC tools with high Return of Investment (such as Security Information & Event Management, Endpoint Detection & Response, Network Detection & Response).
- Mode of SOC operation to be decided such as In-House or Managed Security Service Provider (MssP).
- Understand Mission Priorities.
- Understand the business focus and its missions.
- Identify relevant assets which drive the mission’s success.
- Identify Mission Dependencies.
- Identify dependencies for the mission-critical assets.
- Device Completeness
- Data Field Completeness
- Timeliness
- Consistency
- Retention
- Topic Reference(s): Log Quality Check
- Internet to Intranet (and vice-versa) connection on suspicious ports such as 445, 3389, 22, etc.,
- VPN connections from non-business countries
- Brute Force Login Attempts
- Phishing email
- Intranet Port Scanning
- Industry
- Available Technology
- Geographical Location
- Techniques we can detect
- Techniques we can degrade and deceive
- Techniques we can deny
- Automations to reduce man’s efforts on repeated tasks should be incorporated.
- Vulnerability Assessment gives more visibility about the assets driving with high critical vulnerabilities. Periodic patch management and vulnerability assessment hand in hand provide more visibility to the security posture of the organization.
- The process of threat hunting is briefed in one of the writings earlier. Follow this link for more details.
- Threat Emulation will help organizations to understand their capability to detect when a threat profiled adversaries in conducting their operation against the environment. The mimicked Techniques need to be emulated and the security use case alerting efficiency needs to be validated post emulation activity.
- As mentioned in the introduction, the stages are iterative processes and keep changing as the organization’s mission changes, and priority changes. The below picture shows the repeat loop of the stages which will be iterated over a period of time.
- Repeat Q : Operates when your emulation exercise output shows proven detection gaps which need to be fixed.
- Repeat W : Operates when you business mission changes, priority changes and the environment expands.
Infancy.M3 – Mode of Operation
Age I
This stage is about understanding the environment, business and assets which are high-value targets for an attacker.
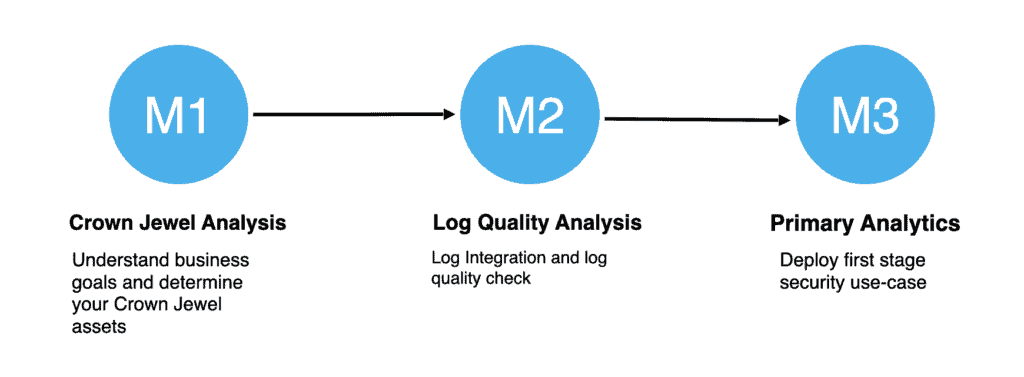
Age:I.M1 – Crown Jewel Analysis
Topic Reference(s): MITRE CJA
Age:I.M2 – Log Quality Analysis
Integrate the assets with centralized management solutions such as Security Information & Event Management(SIEM). Post integration, the logs should be subjected to the below checks to ensure it adds value to our security monitoring,
Age:I.M3 – Primary Analytics
In this stage, we will build our first set of use cases to detect anomalies around our crown jewel assets. Below are the few categories of use cases (feel free to add more based on your environment)
NOTE: Age:I.M3 might produce high False Positive alerts if we haven’t understood the environment better
(both N–>S and E–>W traffic behavior to be gathered and excluded as part of known behaviors)
Age II
This stage is more of an intelligence-driven approach to detect, alert, and degrade attackers’ actions against an environment.
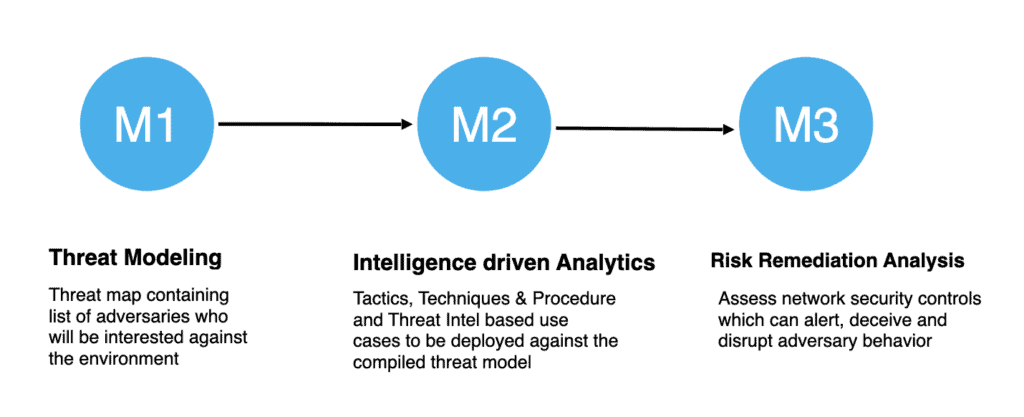
Age:II.M1 – Threat Modeling
In this stage, we will gather the list of adversaries who might be interested against your crown jewel assets. The adversaries might land in your environment based on below factors,
The output of this stage will produce an adversary list from whom we will defend our network.
NOTE: Say for example, our output from previous step has given APT29 and APT 30 as our adversary and going forward this adversary profile is called “Threat Book”
Topic Reference(s): Threat Modeling
Age:II.M2 – Intelligence-driven Analytics
From the previous stage (Age:II.M1) output we have compiled a TTP map for the adversaries,
The combination of TTP by both threat groups is compiled with the help of MITRE Navigator and the output will look something like this. Now we have a list of TTPs for which we need to create detection use cases. There are plenty of resources which will help build the use case repository. Listing a few sites for reference,
NOTE: IOC based intelligence to detect our “Threat Book” should be collected with the help of Threat Intelligence Platform such as MISP.
Age:II.M3 – Risk Remediation Analysis
During this stage, we will analyze the list of security controls which will be helpful in defending against the adversary TTPs(in our case APT29 and APT30). This is a hands-off exercise to understand the detection, deny, degrade and deceive capabilities of the security tools and map them to MITRE matrix against our “Threat Book” TTPs.
Research Topic: Upon research, I found MITRE Engenuity security-stack-mapping for Azure and AWS.This is still a research topic for me wherein I am looking for something more similar to Engenuity project for on-premise IT environment. Topic Reference(s): Risk Remediation Analysis; SOC Assessment
Age III
During this stage, more proactive actions are conducted which helps SOC to respond faster to cyber threats.
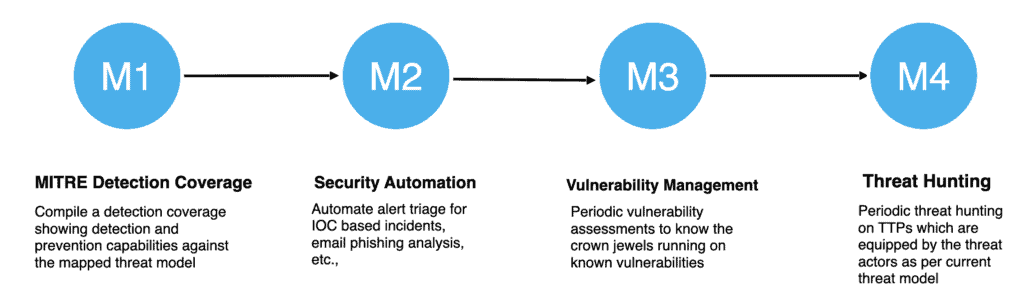
Age:III.M1 – MITRE Detection Coverage
Based on the stage (Age:II.M1) we know the list of TTP to detect and from stages (Age:II.M2) & (Age:II.M3) we can compile a matrix which portrays the list of TTP we can detect, alert, deceive and degrade the attacker’s progress.
Create a MITRE Att&ck layer combining all the three and have a clear understanding of the below,
Based on the above we might end up with few TTPs remaining untouched by all categories (deny, detect, deceive or degrade). Detailed research should be conducted against the list and threat-informed decisions need to be made (either enable logging or purchase new security controls)
Topic Reference(s): MITRE Navigator
Research Topic: Looking for a way to map the output of this stage into node weights against each crown jewel asset. The final crown jewel asset dependency graph should contain node dependency link, node risk value which help defenders to understand their current capability and the area to focus.
Age:III.M2 – Security Automation
Age:III.M3 – Vulnerability Management
Age:III.M4 – Threat Hunting
Age IV
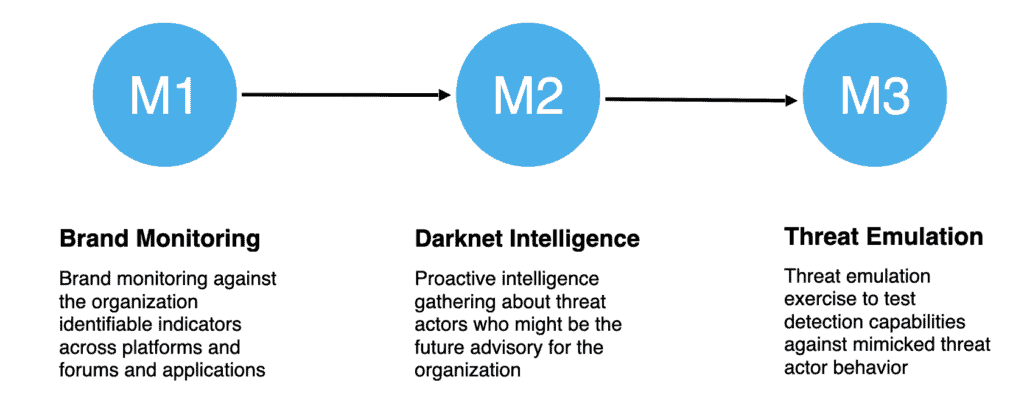
Age:IV.M3 – Threat Emulation
Topic Reference(s): Threat Emulation; Caldera
SOC Iteration Model
Author:
Kaviarasan Asokan
MDR Lead, CyberGate
